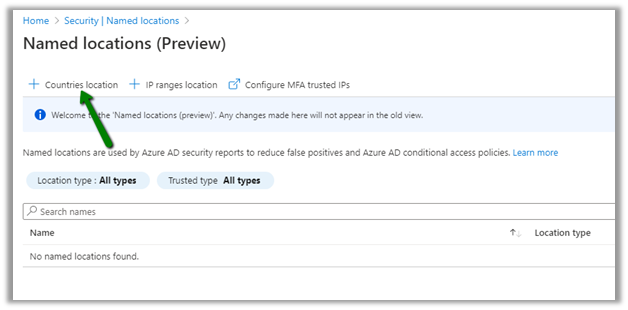
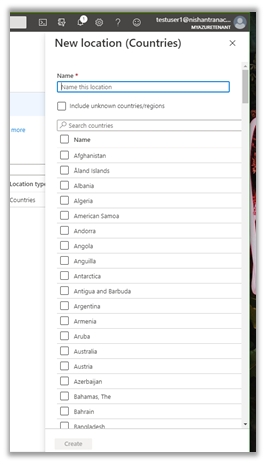
The below error occurs for the application registered with Azure AD (Delegated Permissions), which requires either user or an administrator’s consent for the permissions it needs.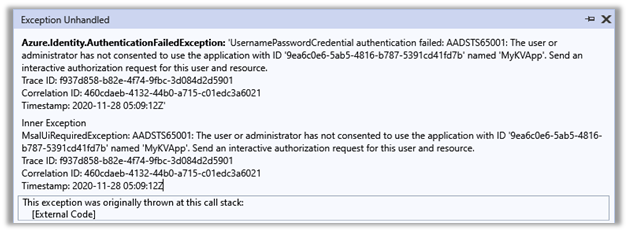
“Azure.Identity.AuthenticationFailedException: ‘UsernamePasswordCredential authentication failed: AADSTS65001: The user or administrator has not consented to use the application with ID ‘9ea6c0e6-5ab5-4816-b787-5391cd41fd7b’ named ‘MyKVApp’. Send an interactive authorization request for this user and resource.”
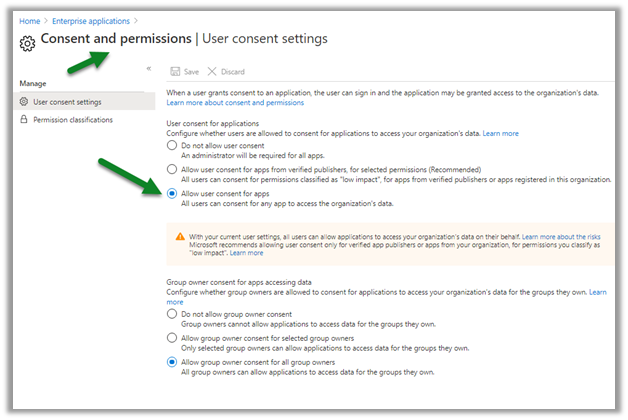
The below setting specifies that all users can allow applications to access the organization’s data on their behalf.
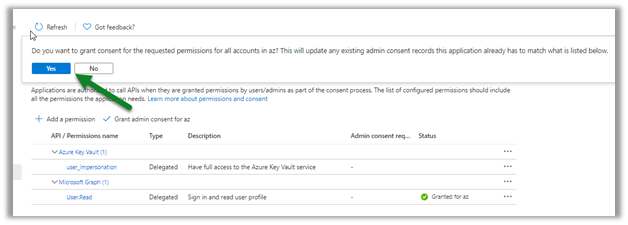
Here the admin can grant the consent through the portal as shown below from Home > App > API Permissions

or can also use Consent URL
https://login.microsoftonline.com/{tenant-id}/adminconsent?client_id={client-id}

When trying to access the consent URL using another non-admin user, we might get the below message, which means that only the admin can provide the required consent.

Signing in with the Admin account presents the below message for granting the app the required permissions.

Admin can also revoke the admin consent (along with the permission as shown below) from the portal as shown below through Remove admin consent option.

Get all the details here –
Hope it helps..